| Author: | |
| Website: | |
| Page title: | |
| URL: | |
| Published: | |
| Last revised: | |
| Accessed: |
Wireless communication is invaluable in situations where the use of guided media may pose problems, and the huge demand for wireless connectivity (for mobile phones, portable computers and personal data assistants for example) is fuelling the proliferation of wireless technology. Microwave frequencies in the range 2.400 - 2.484 GHz do not require a licence, and are therefore popular for short range applications, and line-of-sight wireless links can be established between two local area networks using microwave or laser links where a cable connection would be difficult or prohibitively expensive to implement. A wireless LAN (WLAN) is a local area network based on wireless technology. Most modern local area networks now employ some wireless network infrastructure because it allows existing networks to be extended without the expense of additional cabling, and allows users of portable network devices to maintain connectivity with the network as they move around. Wireless networks can be set up quickly and can be configured in either ad hoc or infrastructure mode. In ad hoc mode, two or more portable computers can communicate with each other in the wireless equivalent of a peer-to-peer network. There is no connection to a wired network and a wireless access point is not required.

An ad hoc wireless network
The infrastructure mode relies on one or more wireless access point to provide the connection between the various wireless devices. The access point is the wireless equivalent of an Ethernet hub or switch, and is usually connected directly to a wired network so that the wireless devices can communicate not only with each other, but with any other devices attached to the network. The effective range can vary from 20 to 500 metres. The access point itself is usually mounted in an elevated position on a wall or ceiling to maximise its effective range. The placement of multiple access points is often chosen to facilitate hand-off from one access point to another as users move around a building or campus. This concept is illustrated below.
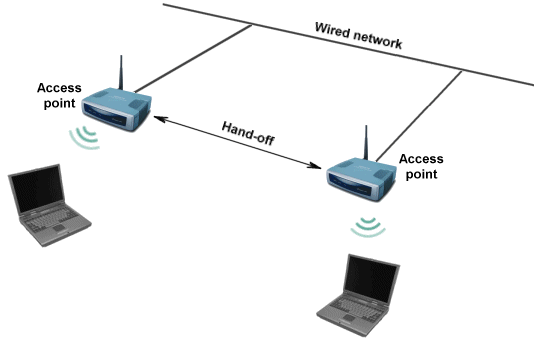
An infrastructure wireless network
Devices that wish to communicate with the WLAN must be equipped with a wireless network adapter. These are available in a variety of form factors just like network adapters intended for use with cables, but will be equipped with an antenna rather than a BNC or RJ45 socket. Wireless equipment operating in the 2.4 GHz frequency range is susceptible to interference from microwave ovens, cordless phones and Bluetooth devices. Wireless networks are increasingly used to provide network connectivity in a home or a small office environment or in other situations where wired connectivity is inconvenient or user mobility is important. It is becoming commonplace to find wireless "hotspots" in airports, railway stations and other public places that allow mobile users within range to connect to the Internet free of charge.
IEEE 802.11 is a set of standards for WLANs that first emerged in 1997. Revised versions were published in 1999 and more recently in 2007, and incorporate the various amendments that have been made to the standard over the years. The first widely accepted amendment to the standard was IEEE 802.11b (released in 1999), which provides a maximum net bit-rate of 11 Mbps and a range of 45-90 metres, and uses Direct Sequence Spread Spectrum (DSSS) signalling in the 2.4 GHz ISM band. IEEE 802.11g (released in 2003) also operates in the ISM band and has a similar range, but uses orthogonal frequency division multiplexing (OFDM) signalling and provides a maximum net bit-rate of 54 Mbps. Most current wireless products support both standards. The IEEE 802.11n standard (released in 2009) can operate at both 5 GHz and 2 GHz, and provides a net bit-rate of up to 600 Mbps with a range of 91-182 meters. It adds a number of new features to those provided by previous versions, including multiple-input multiple-output (MIMO).
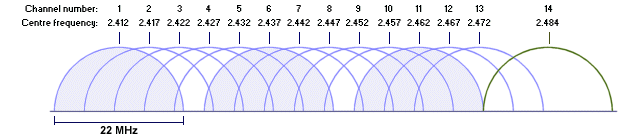
IEEE 802.11 channels in the 2.4 GHz band
The 2.4000–2.4835 GHz band is divided into thirteen channels, each with a width of 22 MHz but spaced only 5 MHz apart. Channel 1 has a centre frequency of 2.412 GHz and channel 13 is centred on 2.472 GHz. To avoid channels overlapping, therefore, they need to be spaced as shown above (for example channels 1, 6 and 11 may be used within the same coverage area without interfering with each other). The channels that may legitimately be used vary from one region to another. In most of Europe, all thirteen channels can be used, while Japan adds an additional channel (channel 14).
Each IEEE 802.11 frame has a header, a variable length payload, and a Frame Check Sequence (FCS). Frames may be control frames, data frames, or management frames. The frame is preceded by a preamble and a Physical Layer Convergence Protocol (PLCP) header, as shown below.
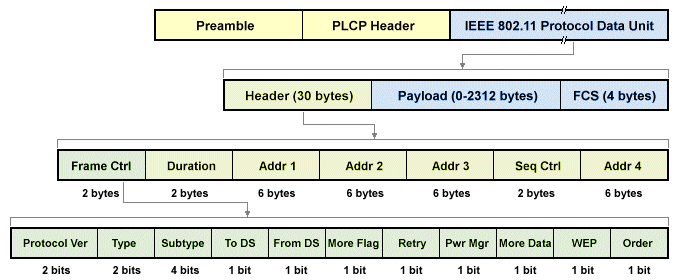
IEEE 802.11 frame format
The first two bytes of the IEEE 802.11 header are taken up by the frame control field, which consists of a number of sub-fields that contain information about the frame, such as the protocol version, frame type, whether power management is active, and so on. The address fields carry the MAC address of the source and destination devices, as well as that of one or more access points. The sequence control field is used for ordering message fragments, and for the identification of any duplicated frames. The variable-length payload can carry user data or control and management information, depending on the frame type. The Frame Check Sequence occupies the last 4 bytes of the frame, and is used for error detection purposes.
Because wireless networks involve the broadcasting of data using radio frequencies, the exchange of information is vulnerable to interception. For this reason it is essential to protect data transmitted wirelessly using some form of encryption. The first wireless encryption scheme to be widely adopted for 802.11 wireless networks was Wired Equivalent Privacy (WEP), which was introduced in 1977. Although still offered as an option for wireless encryption by most wireless devices currently on the market, the limitations of WEP had already started to become apparent by 2001. Today, with the aid of the right software, WEP encryption can be broken within a few minutes. By 2004, WEP had been superseded by Wi-Fi Protected Access (WPA).
Two versions of WEP have seen widespread use, both of which use RC4 encryption. RC4 is a stream cipher that combines plaintext bits with a pseudorandom cipher bit stream (the keystream), typically using a bitwise exclusive-or (XOR) operation. The 64-bit version of WEP uses a 40-bit key, concatenated with a 24-bit initialisation vector to form the RC4 traffic key (the 64-bit limitation produces relatively weak encryption, and was a result of US export restrictions governing cryptographic technology). Following the lifting of export restrictions, a 128-bit version was implemented that uses a 104-bit key, which again is concatenated with a 24-bit initialisation vector to obtain the 128-bit RC4 key. In both versions, the key may be entered either as a string of hexadecimal characters each representing four bits (ten or twenty-six hexadecimal characters, depending on the version) or as an ASCII keyword in which each character represents eight bits (five or thirteen ASCII characters).
WEP provides for two methods of authentication. Open system authentication does not actually require a client to provide its credentials. Effectively, any WLAN client device can authenticate itself with a wireless access point and attempt to establish an association. Once an association has been established, however, the client will require a valid WEP key in order to correctly encrypt or decrypt data frames. The alternative method is shared key authentication, which involves a challenge-response procedure in which the client must correctly encrypt a clear-text challenge phrase using its WEP key. Ironically, it is open system authentication that is the more secure method, since it is possible for an eavesdropper to derive the WEP encryption key used by capturing the challenge and response frames in used in shared key authentication. The most obvious solution to the inherent weaknesses in WEP is to use WPA or WPA2 instead.
The Wi-Fi Protected Access (WPA) protocol was developed as a stop-gap replacement for WEP, pending the development of a more robust authentication and encryption scheme. WPA uses the Temporal Key Integrity Protocol (TKIP) in order to address some of the weaknesses inherent in WEP. Still based on RC4, TKIP has been found to exhibit a number of vulnerabilities and WPA has now been replaced by WPA2. WAP2 uses the far more secure Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) which is based on the Advanced Encryption Standard (AES) rather than RC4. For small office and home (SOHO) networks, the recommended mode of operation is pre-shared key (PSK), in which each wireless device encrypts data using a 256-bit key that is either entered as 64 hexadecimal digits or generated from a pass phrase that can vary in length from eight to sixty-three ASCII characters. For larger wireless networks, authentication may be carried out by an authentication server such as a Remote Authentication Dial In User Service (RADIUS) server.
The IEEE standard covering port-based network access control is IEEE 802.1X, which defines an authentication mechanism for wireless devices that wish to connect with a local area network. A wireless access point acts as the authenticator (basically a security guard for the network), and will not allow a client device to access the network until its identity has been validated and authorisation granted. The credentials provided by the client to the authenticator (i.e. the access point) are passed to an authentication server for verification (note that if the mode of operation is pre-shared key, an access point can verify the client’s credentials and no authentication server is required). If the credentials are valid, the client device is granted access to the network.