The OSI Reference Model
The Open Systems Interconnection (OSI) reference model was developed by the International Standards Organisation (ISO) as a model for computer communications architectures, and as a framework for developing protocol standards. It was intended as a first step towards international standardisation of communications protocols. The model divides the communication process into seven layers, as shown below. The diagram shows how communication takes place indirectly between peer layers at each end of a communications channel (denoted by the bi-directional horizontal arrows), and clearly identifies the concept of an interface between adjacent layers (denoted by the bi-directional vertical arrows).
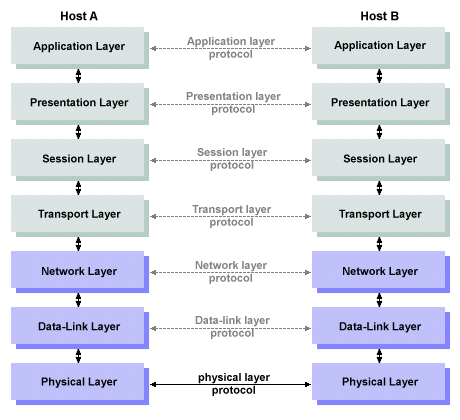
The OSI Reference Model
The OSI Reference Model layers
The model starts at the bottom with the physical layer (layer 1), and ends at the top with the application layer (layer 7). The most important concept behind the model is that each layer performs a specific function, provides services to the layer above it, and uses the services of the layer below it. There is a well-defined interface between each layer, across which the flow of information is kept deliberately minimal. It should be remembered that the OSI model itself is not a communications architecture. It simply specifies what each layer should do, not how this is to be achieved. As shown above, protocols in the same layer at each end of the communications link can communicate with each other only indirectly, by using the services of the layers below them. The individual layers of the OSI Reference Model are summarised below:
- Physical layer - concerned with the physical transmission of a bit stream. Issues include the physical and electrical characteristics of the cables and connections, the encoding and signalling schemes used, and the mechanical, electrical and procedural interfaces. Network devices that operate at this layer include hubs and repeaters.
- Data link layer - the point at which the bit stream enters or leaves the physical layer, and which provides reliable transmission of data across any single network link, including sequencing, flow control and error detection, using hardware addresses. It often defines how devices are connected in terms of the network topology, and how they may access the physical medium. The data link Layer is divided into the logical link control (LLC) sub-layer, which manages the communications link between two devices, and the medium access control (MAC) sub-layer, which manages protocol access to the transmission medium. Network devices that operate at this layer include bridges and switches. Ethernet is an example of a data link layer protocol.
- Network layer - controls the operation of the subnet, and is responsible for the routing and addressing of datagrams (packets) from one network to another using logical addresses (e.g. IP addresses). The most important network devices that operate at this layer are routers. Network layer protocols include the Internet Protocol (IP).
- Transport layer - establishes and terminates connections across the network, and provides a reliable end-to-end transport mechanism for the exchange of data between processes in different end systems. It undertakes flow control, and ensures that data is delivered error-free and in sequence, with no loss or duplication. Typical protocols used at this layer include Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
- Session layer - enables applications on end systems to establish a connection, and provides the mechanism for controlling the dialogue between them.
- Presentation layer - resolves differences in data representation between end systems and encodes data in a standard format for transmission across the network. May also be responsible for providing services such as encryption and data compression.
- Application layer - contains management functions and mechanisms to support distributed applications. Typical protocols used at this layer are File Transfer Protocol (FTP) and the various e-mail protocols.
Data transmission in the OSI model
A process wishing to send data to a process on a remote host passes the data to the application layer protocol, which attaches the appropriate control information (in the form of a header) to the data, creating an application layer protocol data unit (PDU) which is then passed down to the presentation layer. The presentation layer sees the PDU simply as a block of data to be processed. It may transform the PDU in some way, adds its own header, and passes the resulting PDU to the session layer. This process is repeated until the data reaches the physical layer and is transmitted on the physical transmission medium. At the destination host, the protocol operating at each layer reads the control information for that layer, strips off the header, and passes the resulting block of data up to the next layer. Finally, the original data, stripped of all control information, is passed to the target process. This sequence of events is illustrated below.
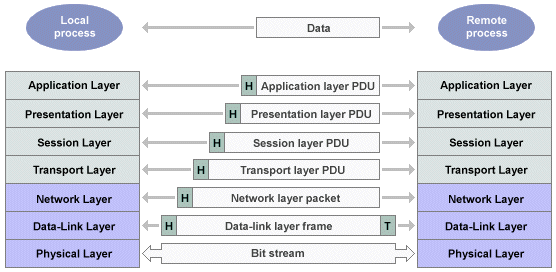
Data transmission in the OSI Reference Model
Advantages and disadvantages of the OSI model
A major advantage of the OSI model is that it clearly distinguishes between the concepts of services, interfaces and protocols. A strictly modular approach to the design of system architecture is encouraged, allowing the protocols operating within each layer to be replaced relatively easily. The purely theoretical basis for the model means that it is not biased towards a particular technological approach, and makes it very useful as a reference model, although it also means that the model does not benefit from practical experience, as a result of which some fairly arbitrary decisions have been made about what functionality should go into each layer. The session and presentation layers, for example, do not actually do a great deal, whereas the data-link layer has had to be divided into two distinct sub-layers (LLC and MAC). The shortcomings of the OSI model, together with the success of the TCP/IP protocol stack, contributed to the lack of success of subsequent attempts to implement a protocol stack based on the OSI model. That said, the OSI model has proved an extremely useful tool for facilitating the discussion of network architectures.
