| Author: | |
| Website: | |
| Page title: | |
| URL: | |
| Published: | |
| Last revised: | |
| Accessed: |
ALOHA is an access protocol for packet radio networks originally developed at the University of Hawaii, although it can be applied to any shared transmission medium, and was the basis for the Ethernet local area network access protocol. A station can transmit packets at any time, but risks collisions with packets transmitted by other stations. When a packet has been transmitted, the station listens for an acknowledgement for an amount of time equal to the maximum possible round-trip propagation delay plus a small fixed time increment. If no acknowledgement is forthcoming, the packet is retransmitted. If an acknowledgement is not received after repeated transmissions, the station ceases its attempts to transmit the data. A receiving station sends an immediate acknowledgement for a correctly received packet (invalid frames are simply ignored).
Heavy traffic results in many collisions, reducing system efficiency. A variation of the system called Slotted ALOHA was developed, in which time on the channel is divided into time slots equal to the frame transmission time. All stations are synchronised to a central clock, and can only transmit at the beginning of a slot. Frames that overlap do so completely, minimising the amount of time lost due to collisions.
The ALOHA packet radio system
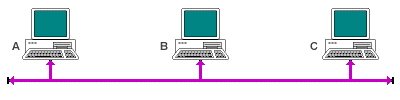
CSMA/CD is the medium access method used by Ethernet networks. Multiple access means that many network devices share a common transmission medium. Carrier sense refers to the fact that stations "listen" to the transmission medium, and transmit only when they cannot detect a transmission from another station. Once a station has started to transmit data, it monitors the transmission medium until all of the the data has been sent. If another station on the network has started to transmit data at the same time, the two signals will "collide" and interfere with each other. Each station involved will detect this interference (collision detection), and interpret it as a collision.
Once a collision is detected, all stations involved will stop transmitting and "back off" for a random period of time (called the deferral time) before attempting to retransmit. CSMA/CD is described as a contentious access methodology, because stations compete for use of the transmission medium. For small networks carrying little traffic, CSMA/CD works well. As traffic increases, so does the number of collisions, and the overhead involved in the detection of collisions and the re-transmission of frames that have suffered a collision causes network performance to deteriorate rapidly. The general sequence of events is shown below.
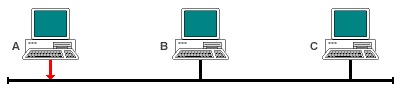
Station A has data to send and starts to transmit
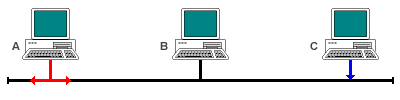
Station B also has data to send and starts to transmit
The signals from station A and B propagate along the network towards each other
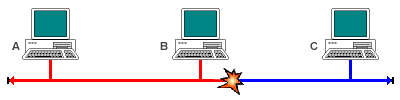
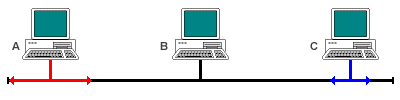
The signals from station A and B collide
The garbled signals are received by all stations, who interpret them as a collision
Token passing is a deterministic methodology for ring networks in which all network devices play some part in managing access to the transmission medium, using a small frame called the token. At any one time, there can be only one token on the ring. The token is passed from station to station around the ring, always in the same direction, in a predetermined sequence. A station must acquire the token in order to transmit data, and may only transmit one frame (or use the token for a limited time) before releasing the token to the next station. The data to be transmitted, together with any required control information, is added to the token to create a data frame. The data frame is transmitted from station to station around the ring until it reaches the destination device, which reads the data, marks the frame as having been received and read, and transmits it to the next station. When the frame arrives back at its point of origin, a new token is generated and is transmitted to the next device on the ring. Each station on the network thus has an equal number of opportunities to transmit data, and since only oner station may transmit at any one time, there are no collisions. The general sequence of events is shown below.
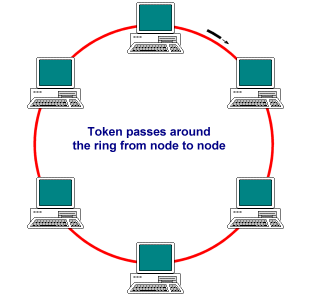
The token circulates continually around the ring
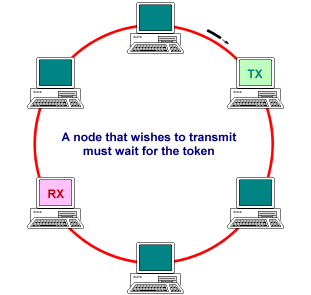
Any device that has data to transmit must first acquire the token
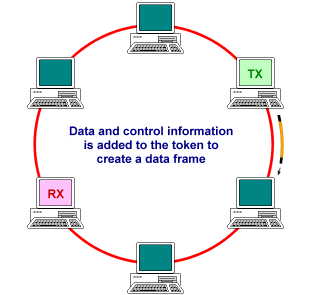
Data and control information is added to the token to create a data frame
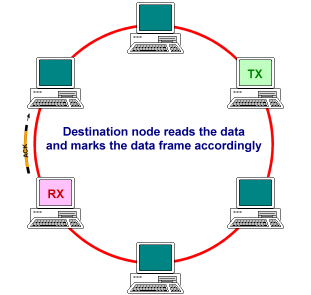
The destination device reads the data and marks the frame accordingly
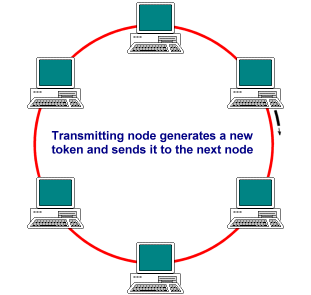
The originating device generates a new frame and transmits it to the next station