| Author: | |
| Website: | |
| Page title: | |
| URL: | |
| Published: | |
| Last revised: | |
| Accessed: |
The implementation process (putting the network design into practice) is probably the most critical stage of the project, as it requires a huge commitment in terms of manpower and financial resources, and can be quite disruptive of the day to day operation of the organisation. The main activities that you might reasonably expect to be undertaken during implementation are listed below.
Note from the above list that testing is an ongoing process and occurs throughout the implementation process. It should not be left until the end of the implementation process, as problems that are not detected and dealt with as they occure will be more difficult to diagnose later, and far more costly to correct.
Network implementation will involve numerous tasks, some of which cannot commence until other tasks have been completed (this is known as a task dependency). The implementation plan should include a description of each task, the proposed start and end dates for the task, and details of any task dependencies. The main project management tool used for implementation scheduling is the Gantt chart, which provides a graphical view of each activity to be undertaken during the implementation phase, showing when each task starts and finishes, and highlighting any task dependencies. A simple example is shown below.
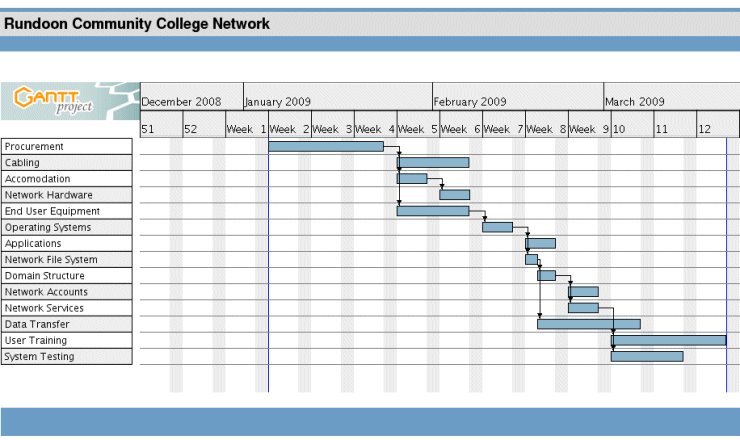
A simplified project schedule Gantt chart
The implementation schedule allows project managers to monitor and control the implementation process. It may include a work schedule for each major task that specifies details of the work to be undertaken, the personnel required to carry out the work, and a list of equipment and materials needed to complete the work. The schedule should also provide details of any unit testing to be carried out during implementation, as well as the post-installation system checks. The report below describes the implementation tasks for the Rundoon Community College network in more detail.
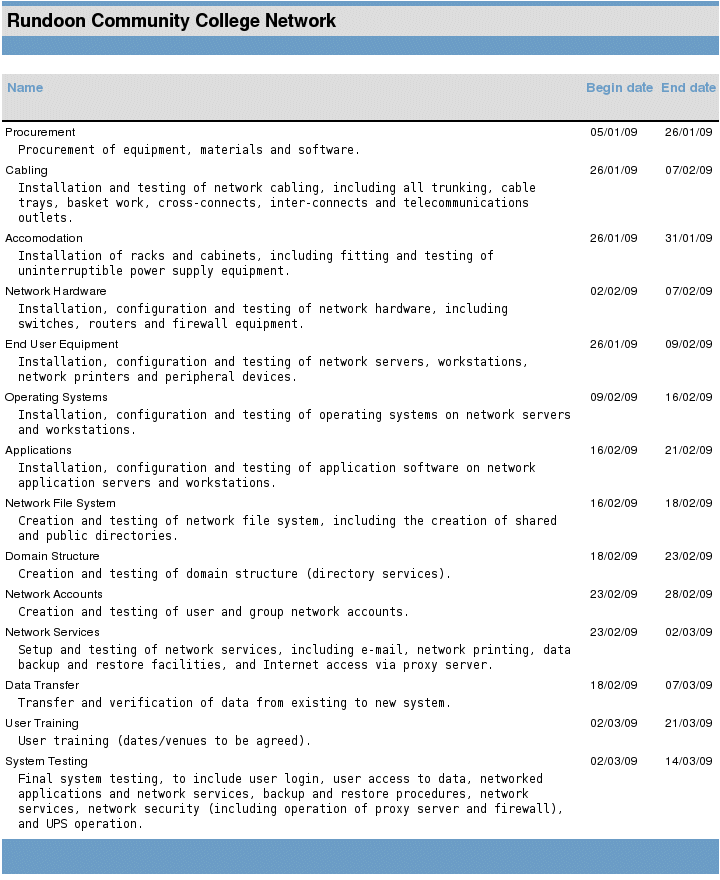
A report describes implementation tasks in more detail
The testing of network cabling, equipment, software and services will be an ongoing process throughout the implementation process. The installation of network cabling will usually be carried out by a specialist cabling company, who will install and test the cables, and provide documentation to certify that the installation meets the required standards. Major items of network equipment such as switches, routers and uninterruptible power supplies will need to be tested for correct operation and configuration after installation. In the case of certain high-value items of equipment (for example, a core switch costing tens of thousands of pounds), the equipment vendor may carry out installation and testing on behalf of the client, and will provide all necessary documentation. Network connectivity and access to user data and applications can be tested by logging into the network from randomly selected workstations using a generic user account (on a large network, it may not be practical to check every single user account individually). Access to email, the Internet, network printing and other services will also be tested. Once the organisation's data has been transferred from the old system to the new system, backup procedures should be rigorously tested to ensure that they function correctly.
Network documentation will include cabling schematics, floor plans showing the location of network equipment, and a detailed technical specification for each item of network hardware. Records should also be maintained of the software installed on each network computer, together with details of software licenses held. The MAC and IP address of each device on the network should also be recorded and cross referenced to a physical location. The availability of detailed and accurate network documentation makes the task of managing and troubleshooting the network and carrying out routine maintenance and repairs a great deal easier. Support can be provided to users far more quickly and effectively if the help desk can identify the installed software, hardware configuration, network address and physical location of a user's workstation before an IT technician is despatched to investigate the problem.
Network security should strike a balance between providing an appropriate level of protection for the organisation's resources, and facilitating user access to those resources. A network security strategy should therefore reduce the level of risk to a minimum without negatively impacting on the productivity of users. Some of the security measures that can be put in place during implementation are outlined below.
One way of improving security is to isolate the organisation's local area network (or networks) from public networks as far as possible by installing a firewall between the local network and external networks. The firewall can be used to implement packet filtering to restrict incoming or outgoing traffic on the basis of its source or destination network address or content type. In addition, unused communication ports can be disabled to prevent unauthorised access to the network via these channels. Internet access can be made more secure by using a proxy server to hide the internal network addresses of LAN clients. Outgoing requests for web resources are routed via the proxy so that remote network hosts will only see the IP address that the proxy server presents to the outside world.
The local network environment should also be protected by anti-virus software, which should be installed on all network computers and updated regularly. Operating system security patches should also be kept up to date, and users should be encouraged to take all reasonable precautions with regard to workstation security, changing their password regularly and not leaving a logged-on workstation unattended.
While many of the security measures implemented will have been decided upon during the design stage, it is during the implementation stage that fine tuning will occur, and the security measures put in place should be tested under operational conditions to ensure there are no unforeseen vulnerabilities.
Training is an important part of network implementation. Users will gain the maximum benefit from new technology only if they are properly trained in its use. Poor training will leave users struggling to utilise network services, creating a negative impact on productivity and resulting in the need for costly technical support. An effective training strategy will begin by determining the training requirements of individual employees, with the aim of finding out what each user needs to know in order to use the network effectively. This may include the use of specific software packages, how to use network services such as email and network printing facilities, or simply how to log in to the network and access shared data. Personnel files should record each user?s level of competency and experience, together with any relevant formal training or qualifications. The job description for each user role should enumerate the applications, resources and services needed in order to carry out the duties thereof.
Although the implementation schedule will probably indicate a time frame in which training should occur, a more detailed training plan should be produced that specifies exactly what training is provided, how and by whom it is implemented, and when and where it will be delivered. Responsibility for staff training should be delegated to an appropriate department or individual within the organisation, who will determine the scope of the training required, prepare training schedules, and procure the necessary training resources.
Training may be conducted in house if the organisation has suitably qualified personnel. Alternatively, or in addition to in-house training, an appropriate training organisation may be contracted to provide specialised training (this is often more cost effective than developing suitable in-house training). The effectiveness of training can only be evaluated once it is put into practice, and the need for further training should not be ruled out. There will inevitably be an ongoing need for training as new personnel are employed or staff move into different roles within the organisation.